Description
The Infinite Noise TRNG combines the best of two worlds. Modular entropy multiplication is used in the open hardware to create provable random data.
It’s cryptographic strength is based on the SHA-3(Keccak) hashing function, implemented in free software.
The hardware continuously reseeds that Keccak sponge to make it even more secure.
So even if an attacker would be able to capture a snapshot of the Keccak state, it’s worthless within a single cycle.
Raw data from modular entropy multiplication has certain properties (actually non-randomness) which are extremely useful:
- The device is not rapidly changing the sort of numbers it puts out, so history can be used as a guide.
- There is no special state stored in the modular entropy multiplier that could cause data to be different each clock cycle, other than on even/odd cycles.
- Bits further away are less correlated.
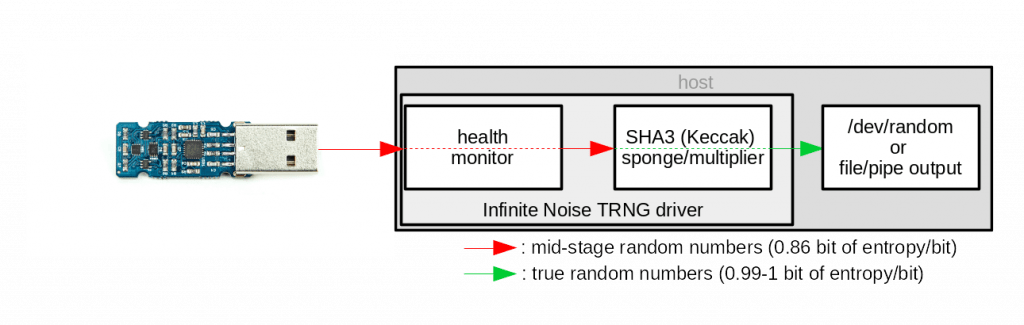
This allows health monitoring on the raw data. Only when its in the expected range, it is passed to the Keccak sponge.
Of course this also means you should not use the raw output for any cryptographic operations.
But you have the freedom of accessing it directly to verify correct operation of the hardware or to apply different whitening functions,
but right now SHA-3 is the best option!
How it works
The hardware derives entropy from thermal noise, like many random number generators. What divides it from other TRNGs is the modular entropy multiplication technique.
Thermal noise of resistors is being amplified in an infinite loop to generate data – which is not totally random yet. By using modular entropy multiplication there is some correlation of adjacent bits in the stream.
Health monitoring of important parameters of the raw data-stream is implemented in the devices driver, which then uses the SHA-3 hashing function for cryptographic whitening to produce true random numbers.
There is no way to override the signal without being noticed by the driver. Of course it’s possible to influence it a bit, but because we use modular entropy multiplication, this only makes the output slightly more random.
Since by definition there are no patterns in random data, how can you know the data coming from your entropy source was not spoofed? The Infinite Noise TRNG produces this predictable level of entropy, just because it’s the only way to constantly verify the hardware is working properly. And only then will it apply whitening with the SHA3 hashing function.
It may sound daunting, but this is the key feature of this implementation, as the foreseeable (and very high) level of entropy enables the driver to monitor proper function of the device. It’s an essential feature for any trustworthy random number generator, which most available devices are lacking. Even when you can access the raw output – during operation you often don’t find a way to monitor their operation.
Key features
- no firmware (that could be modified by an attacker)
- using only stock components (COTS)
- health monitor built into the driver
- free software for GNU/Linux, *BSD and Windows
- open source hardware (OSHWA certified)
Technical Data
- USB2.0 Interface
- 30KByte/s random output
- Dimensions: 50mm (L) x 19mm (W) x 8mm (H)
- Weight: 10g
- Low power consumption of 8mA @ 5V
- Made in Germany
Resources
| Drivers | Downloads & Repositories |
| Github | https://github.com/13-37-org/infnoise |
| Serial number verification | leetronics.de/verify |
| Users Manual | |
| EU Declaration of Conformity |
FAQ
Driver
How to verify the package signature?
1. Get the key fingerprints
The fingerprints of the code signing key used for all the packages and repositories can currently be found in four different locations:
- Crowd Supply campaign
- GitHub
- 13-37.org
- the user manual (link below)
After you did this, continue with the installation as described on Linux packages for the Infinite Noise TRNG
2. Download and verify the public key
$ wget -O 13-37.org-code.asc https://13-37.org/files/pubkey.gpg
Verify the keys fingerprint:
# GPG1
$ gpg --with-fingerprints 13-37.org-code.asc
# GPG2:
$ gpg2 --import-options import-show --dry-run --import < 13-37.org-code.asc3.1 Debian/Ubuntu
Add the public key to apt’s keyring:
$ sudo apt-key add 13-37.org-code.gpg3.2 RPM
Import the public key to rpm’s keyring:
$ rpm --import 13-37.org-code.asc
3.3 ArchLinux
TODO
How to compile the driver?
To compile the driver, you’ll need the libftdi development files installed. Usually called libftdi-dev – or also compile it from source.
$ git clone https://github.com/13-37-org/infnoise/
$ cd infnoise/software
$ make -f Makefile.linux
$ make install
The udev rule in software/init_scripts may not be installed properly this way. See the software’s README on github fore more details.
When running infnoise, I get “USB read or write failed” after some seconds
Each instance of the driver uses the corresponding USB device exclusively, so its not possible to run the driver twice – and trying to do so will result in these error messages.
Make sure you have stopped the Infinite Noise service, as it will try to restart – causing that error. If you’re using it behind an USB hub, try connecting it directly to your port. (Or try another USB port)
# sudo service infnoise.service stop
Optionally, you can also mask the service so it also won’t be restarted if you plug in the device.
# sudo systemctl mask infnoise.service
If all this doesn’t help, please contact us as this may indicate a problem with the hardware.
Is it possible to use multiple devices in parallel?
Yes – we can! But only on Linux (so far).
There are different scenarios in which this may be useful, as you can have only one session per device.
1. You want to use it in /dev/random mode and use the binary to play with random data at the same time
You could stop the service with service infnoise stop so you can execute infnoise without problems. Otherwise systemd will kick you out again (and you’ll se the error message USB read/write failed) as it tries to restart the driver.
The supplied systemd unit file reads a configuration file in /etc/infnoise.conf where you can INFNOISE_SERIALaccording to the device to be used for /dev/random mode – and use further devices for whatever you want.
If you don’t want it to start at all – just disable it with systemctl mask infnoise.
2. You need more speed
When you have a custom application requiring huge amounts of random data, you can attach at least 10 devices in parallel – as I do for production testing (at a single USB hub!).
Just be aware this may cause a lot of cpu load – especially when you want to combine it a huge whitening multiplier – and you’ll need to merge the data streams somehow (or use one device per thread?).
Note: Don’t use other devices on the same USB hub – and even better use a real port for each device, as timing issues may arise.
How To Use
There are several different ways to consume the entropy.
/dev/random (only works with GNU/Linux)
Just let it feed /dev/random and feel a bit safer while accelerating your cryptographic operations when you do lots of them.
This is the default mode of operation of the downloadable packages as feeding the kernel’s entropy pool is the simplest way to get entropy to where its needed.
The systemd service used to start the driver configuration file /etc/infnoise.conf where you can change some parameters used in this mode of operation.
Note: Remember to stop the service before using the other ways described below.
$ sudo service infnoise stop
When you don’t want it to start when you plugin the device, you can disable it permanently with:
$ sudo systemctl mask infnoise.serviceRun it from the command line
Execute the binary and capture its stdout for further processing (Windows, MacOS and GNU/Linux)
You can simply run the infnoise command with its various parameters command after compiling it from source or installing the compiled and signed packages.
Keep in mind you need to stop other instances running on the same device.
Integrate into your custom application
Call the binary within your custom application and capture stdout and optionally also stderr to use the data while monitoring the health monitor.
There are some usage examples for this on GitHub.
There is also a shared C library (libinfnoise) to built upon. Examples are also on Github (see above).
Hardware
Why is whitening not implemented in hardware?
The Infinite Noise does not have microcontroller capable of this. It uses an off-the-shelf usb chip to interface with your computer. This way there is no programmable logic in the signal path. See update #3 for details.
Why this is an essential security feature? As the driver always sees the raw stream from the device, it is able to constantly verify the data is OK to use.
Why does it have no firmware?
By using an off-the-shelf usb chip there is no reprogrammable logic in the signal path. This is great as it reduces the attack vectors on the device dramatically.
See updates #3 and #5 of the Crowd Supply campaign for more details.
How can it have a serial when there is no firmware?
The USB chip has no re-programmable logic, but still offers us access to an EEPROM to save application or USB specific data like the Vendor- and Product-ID’s as well as an usually factory programmed serial number (i.e. DM00WOEF)
In the first place, I did not want to change the EEPROM settings at all and just use the “unique” serial numbers from FTDI. But as we’ve been getting close to the 5000$ goal so fast, I continued working on the workflow to create the labels.
It turned out to be very complicated to read-out the actual serial number and print (super-small) labels one by one. And I wasn’t so sure about the uniqueness of FTDI’s serial numbers. That’s why a new serial number is assigned from a database of pre-generated ones right after the final production test has passed. The dataset of the specific serial number is completed with the test results, a batch number, the “unique” FTDI serial and a timestamp.
By integrating this into the automated workflow of device testing I just need to put the right label onto the device (and my script tells me which one goes where).
How can I restore its original serial
Yes you can! Using the FTDI FT_Prog utility for Windows this is pretty easy. There is also a command line tool ftdi_eeprom included in the fully open-source FTDI driver that I’m using in the production workflow – buts its very low-level.
Using the online verification service you can download a generated config file to restore it’s original or its production serial, using the .CONF for the Linux tool or .XML for Windows/FT_Prog.
If you have removed the security label (or did not have one), write down your original serial number before you continue, otherwise you might lose it forever. There is no way for me to associate the serial numbers to purchases, so I won’t be able to help you. Warranty claims are of course still possible, as long as you have the invoice/order receipt.
Modular Entropy Multiplication and SHA-3
Some important aspects of modular entropy multiplication and the Keccak SHA-3 sponge used for whitening.
Why not use the raw output directly?
Of course you can access the raw output stream by using --raw – but has only 286.000 bits of entropy in 300.000 bits. Anyway its a very reliable source of true random numbers to feed into a hashing function (like SHA-3). If you want to feed it into a different whitening algorithm – using --raw is an option. When going this way its probably easier to integrate it in the existing open source driver (and share).
How does the output multiplier work?
Normally the driver reads as many bytes from the Keccak sponge as raw data was put in. As we read the full buffer of the USB chip at once, this is always 64 bytes/512 bits of entropy per round.
Using the multiplier the data rate be extended to 256 * MULTIPLIER bits with (almost) no degradation in entropy.
Data is still read in chunks of 1024 bits between each permutation of the Keccak state, to not compromise the full internal state (which has 1600bit/200 bytes). After 256*MULTIPLIER bits have been read, it is reseeded with 512 bits of raw entropy. The full Keccak state is never exposed, as this would allow attacks on it.

























Kim Sindalsen –
Simply works™ – Switched from ubld.it TrueRNG to this – my machines often didn’t boot correctly with the TrueRNG left in the usb slot (had to be inserted during startup on my PCEngines APU-boards).
This I can leave in during reboot + they provide entropy at a higher rate.
Nicht verifizierter Kauf. Mehr Informationen
Marvin –
Can confirm, it just works. The software is simple to use and the hardware works as advertised. A great addition to my collection.
Verifizierter Kauf. Mehr Informationen
Søren Grønning –
I’ve bought two of these TRNG USB dongles and both arrived in a timely manner, no need to email or otherwise contact 13-17.org / leetronics.de for this to happen.
Installing the driver from Debian’s software repositories, everything just works as expected, hugely driving up my entropy pool on my Raspberry Pi or even my Mac Mini 2011!
Great job!
Verifizierter Kauf. Mehr Informationen
Alexander –
Hey, I bought item loong ago. Was in the same situation as commentators. Main issue – contact from owner. Very long response, long delivery time. I think this is the biggest problem here. Do not worry, you’ll get your device but not soon. This is all understandable because this project is more of a hobby than making money. If you really need such a device, you can find it here. The service will hopefully improve as the community grows.
Verifizierter Kauf. Mehr Informationen
Jan –
I bought two devices and received them a few days later. They work like a charm. (There is only a small problem with udev rules under sysV Devuan…)
Verifizierter Kauf. Mehr Informationen
Bee –
Two weeks after I ordered I sent a status inquiry by email. My random number generator was then shipped within a day. Then the postal service in my country sat on it for 12 days without explanation. Eventually it arrived, and the hardware seems to work as far as I can tell.
On the software side there are some issues. In particular, SystemD believes that the device disappears immediately after it appears, and thus stops the daemon after a few milliseconds. Yet when I run Infnoise manually it can access the device just fine. Only when I boot with the random number generator inserted is the daemon allowed to continue running. If it turns out to work reliably on every boot, that will be good enough, as I was going to leave it constantly attached anyway.
Verifizierter Kauf. Mehr Informationen